In this tutorial, you'll learn how to integrate Cisco AnyConnect with Azure Active Directory (Azure AD). When you integrate Cisco AnyConnect with Azure AD, you can:
- Control in Azure AD who has access to Cisco AnyConnect.
- Enable your users to be automatically signed-in to Cisco AnyConnect with their Azure AD accounts.
- Manage your accounts in one central location - the Azure portal.
Prerequisites
There is no integration or any integration necessary. If the system is managed by Intune, then it will receive what you've configured it to receive whether you use AnyConnect or not. If there are prerequisites for AnyConnect, then you need to configure Intune to deploy them. Also, this isn't an Intune forum, it's a ConfigMgr forum. Windows anyconnect-win-version-predeploy-k9.zip macOS anyconnect-macos-version-predeploy-k9.dmg. Step2 InstructuserstouncheckCisco AnyConnect VPN Module. In my previous post, I talked about the new VPN support for user-driven Hybrid Azure AD Join. I described the key VPN requirements: The VPN connection either needs to be automatically established (e.g. “always on”) or it needs to be one that the user can manually initiate from the Windows logon screen. We don't have any change log information yet for version 4.8.03052 of Cisco AnyConnect Secure Mobility Client. Sometimes publishers take a little while to make this information available, so please check back in a few days to see if it has been updated.
To get started, you need the following items:
- An Azure AD subscription. If you don't have a subscription, you can get a free account.
- Cisco AnyConnect single sign-on (SSO) enabled subscription.
Scenario description

In this tutorial, you configure and test Azure AD SSO in a test environment.
- Cisco AnyConnect supports IDP initiated SSO
Adding Cisco AnyConnect from the gallery
To configure the integration of Cisco AnyConnect into Azure AD, you need to add Cisco AnyConnect from the gallery to your list of managed SaaS apps.
- Sign in to the Azure portal using either a work or school account, or a personal Microsoft account.
- On the left navigation pane, select the Azure Active Directory service.
- Navigate to Enterprise Applications and then select All Applications.
- To add new application, select New application.
- In the Add from the gallery section, type Cisco AnyConnect in the search box.
- Select Cisco AnyConnect from results panel and then add the app. Wait a few seconds while the app is added to your tenant.
Configure and test Azure AD SSO for Cisco AnyConnect
Configure and test Azure AD SSO with Cisco AnyConnect using a test user called B.Simon. For SSO to work, you need to establish a link relationship between an Azure AD user and the related user in Cisco AnyConnect.
To configure and test Azure AD SSO with Cisco AnyConnect, perform the following steps:
- Configure Azure AD SSO - to enable your users to use this feature.
- Create an Azure AD test user - to test Azure AD single sign-on with B.Simon.
- Assign the Azure AD test user - to enable B.Simon to use Azure AD single sign-on.
- Configure Cisco AnyConnect SSO - to configure the single sign-on settings on application side.
- Create Cisco AnyConnect test user - to have a counterpart of B.Simon in Cisco AnyConnect that is linked to the Azure AD representation of user.
- Test SSO - to verify whether the configuration works.
Configure Azure AD SSO
Follow these steps to enable Azure AD SSO in the Azure portal.
In the Azure portal, on the Cisco AnyConnect application integration page, find the Manage section and select single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set up single sign-on with SAML page, click the edit/pen icon for Basic SAML Configuration to edit the settings.
On the Set up single sign-on with SAML page, enter the values for the following fields:
a. In the Identifier text box, type a URL using the following pattern:
< YOUR CISCO ANYCONNECT VPN VALUE >b. In the Reply URL text box, type a URL using the following pattern:
< YOUR CISCO ANYCONNECT VPN VALUE >Note
These values are not real. Update these values with the actual Identifier and Reply URL. Contact Cisco AnyConnect Client support team to get these values. You can also refer to the patterns shown in the Basic SAML Configuration section in the Azure portal.
On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Certificate (Base64) and select Download to download the certificate file and save it on your computer.
On the Set up Cisco AnyConnect section, copy the appropriate URL(s) based on your requirement.
Note
If you would like to on board multiple TGTs of the server then you need to add multiple instance of the Cisco AnyConnect application from the gallery. Also you can choose to upload your own certificate in Azure AD for all these application instances. That way you can have same certificate for the applications but you can configure different Identifier and Reply URL for every application.
Create an Azure AD test user
In this section, you'll create a test user in the Azure portal called B.Simon.
- From the left pane in the Azure portal, select Azure Active Directory, select Users, and then select All users.
- Select New user at the top of the screen.
- In the User properties, follow these steps:
- In the Name field, enter
B.Simon. - In the User name field, enter the username@companydomain.extension. For example,
B.Simon@contoso.com. - Select the Show password check box, and then write down the value that's displayed in the Password box.
- Click Create.
- In the Name field, enter
Assign the Azure AD test user

In this section, you'll enable B.Simon to use Azure single sign-on by granting access to Cisco AnyConnect.
- In the Azure portal, select Enterprise Applications, and then select All applications.
- In the applications list, select Cisco AnyConnect.
- In the app's overview page, find the Manage section and select Users and groups.
- Select Add user, then select Users and groups in the Add Assignment dialog.
- In the Users and groups dialog, select B.Simon from the Users list, then click the Select button at the bottom of the screen.
- If you are expecting a role to be assigned to the users, you can select it from the Select a role dropdown. If no role has been set up for this app, you see 'Default Access' role selected.
- In the Add Assignment dialog, click the Assign button.
Configure Cisco AnyConnect SSO
You are going to do this on the CLI first, you might come back through and do an ASDM walk-through at another time.
Connect to your VPN Appliance, you are going to be using an ASA running 9.8 code train, and your VPN clients will be 4.6+.
First you will create a Trustpoint and import our SAML cert.
The following commands will provision your SAML IdP.
Now you can apply SAML Authentication to a VPN Tunnel Configuration.
Note
There is a feature with the SAML IdP configuration - If you make changes to the IdP config you need to remove the saml identity-provider config from your Tunnel Group and re-apply it for the changes to become effective.
Create Cisco AnyConnect test user
In this section, you create a user called Britta Simon in Cisco AnyConnect. Work with Cisco AnyConnect support team to add the users in the Cisco AnyConnect platform. Users must be created and activated before you use single sign-on.
Test SSO
In this section, you test your Azure AD single sign-on configuration with following options.
- Click on Test this application in Azure portal and you should be automatically signed in to the Cisco AnyConnect for which you set up the SSO
- You can use Microsoft Access Panel. When you click the Cisco AnyConnect tile in the Access Panel, you should be automatically signed in to the Cisco AnyConnect for which you set up the SSO. For more information about the Access Panel, see Introduction to the Access Panel.
Next Steps
Once you configure Cisco AnyConnect you can enforce session control, which protects exfiltration and infiltration of your organization’s sensitive data in real time. Session control extends from Conditional Access. Learn how to enforce session control with Microsoft Cloud App Security.
Introduction
This document describes how to configure Security Assertion Markup Language (SAML) with a focus on Adaptive Security Appliance (ASA) AnyConnect through Microsoft Azure MFA.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Basic knowledge of RA VPN configuration on ASA.
- Basic knowledge of SAML and Microsoft Azure.
- AnyConnect Licenses enabled (APEX or VPN-Only).
Components Used
The information in this document is based on these software and hardware versions:
- A Microsoft Azure AD subscription.
- Cisco ASA 9.7+ and Anyconnect 4.6+
- Working AnyConnect VPN profile
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
SAML is an XML-based framework for exchanging authentication and authorization data between security domains. It creates a circle of trust between the user, a Service Provider (SP), and an Identity Provider (IdP) which allows the user to sign in a single time for multiple services. Microsoft Azure MFA seamlessly integrates with Cisco ASA VPN appliance to provide additional security for the Cisco AnyConnect VPN logins.
SAML Components
Metadata: It is an XML based document that ensures a secure transaction between an IdP and an SP. It allows the IdP and SP to negotiate agreements.
Roles supported by the devices (IdP, SP)
A device may support more than one role and could contain values for both an SP and an IdP. Under the EntityDescriptor field is an IDPSSODescriptor if the information contained is for a Single Sign-On IdP or a SPSSODescriptor if the information contained is for a Single Sign-On SP. This is important since the correct values must be taken from the appropriate sections in order to set up SAML successfully.
Entity ID: This field is a unique identifier for an SP or an IdP. A single device might have several services and can use different Entity IDs to differentiate them. For example, ASA has different Entity IDs for different tunnel-groups that need to be authenticated. An IdP authenticating each tunnel-group has a separate Entity ID entries for each tunnel-group in order to accurately identify those services.
ASA can support multiple IdPs and has a separate entity ID for each IdP to differentiate them. If either side receives a message from a device that does not contain an entity ID that has been previously configured, the device likely drops this message, and SAML authentication fails. The Entity ID can be found within the EntityDescriptor field beside entityID.
Service URLs: These define the URL to a SAML service provided by the SP or IdP. For IdPs, this is most commonly the Single Logout Service and Single Sign-On Service. For SPs, this is commonly the Assertion Consumer Service and the Single Logout Service.
The Single Sign-On Service URL found in the IdP metadata is used by the SP to redirect the user to the IdP for authentication. If this value is incorrectly configured, the IdP does not receive or is unable to successfully process the Authentication request sent by the SP.
The Assertion Consumer Service URL found in the SP metadata is used by the IdP to redirect the user back to the SP and provide information about the user's authentication attempt. If this is configured incorrectly, the SP does not receive the assertion (the response) or is unable to successfully process it.
The Single Logout Service URL can be found on both the SP and the IdP. It is used to facilitate logging out of all SSO services from the SP and is optional on the ASA. When the SLO service URL from the IdP metadata is configured on the SP, when the user logs out of the service on the SP, the SP sends the request to the IdP. Once the IdP has successfully logged the user out of the services, it redirects the user back to the SP using the SLO service URL found within the SP’s metadata.
SAML Bindings for Service URLs: Bindings are the method the SP uses to uses to transfer information to the IdP and vice versa for services. This includes HTTP Redirect, HTTP POST, and Artifact. Each method has a different way of transferring data. The binding method supported by the service is included within the definition of that services. For example: SingleSignOnService Binding='urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect' Location='https://saml.example.com/simplesaml/saml2/idp/SSOService.php'/ >. The ASA does not support the Artifact binding. ASA always uses the HTTP Redirect method for SAML authentication requests, so it is important to choose the SSO Service URL that uses the HTTP Redirect binding so that the IdP expects this.
Certificates for Signature and Encryption Operations
To provide confidentiality and integrity for the messages sent between the SP and the IdP, SAML includes the ability to encrypt and sign the data. The certificate used to encrypt and/or sign the data can be included within the metadata so that the receiving end can verify the SAML message and ensure that it comes from the expected source. The certificates used for signing and encryption can be found within the metadata under KeyDescriptor use='signing' and KeyDescriptor use='encryption', respectfully, then X509Certificate. The ASA does not support encrypting SAML messages.
Network Diagram
Configure
Add Cisco AnyConnect from the Microsoft App Gallery
Step 1. Log in to Azure Portal and select Azure Active Directory.
Step 2. As shown in this image, select Enterprise Applications.
Step 3. Now select New Application, as shown in this image.
Step 4. In the Add from the gallery section, type AnyConnect in the search box, select Cisco AnyConnect from the results panel, and then add the app.
Step 5. Select the Single Sign-on menu item, as shown in this image.
Step 6. Select SAML, as shown in the image.
Step 7. Edit Section 1 with these details.
Step 8. In the SAML Signing Certificate section, select Download to download the certificate file and save it on your computer.
Step 9. Note this, it is required for ASA configuration.
- Azure AD Identifier - This is the saml idp in our VPN configuration.
- Login URL - This is the URL sign-in.
- Logout URL - This is the URL sign-out.
Assign Azure AD User to the App
In this section, Test1 is enabled to use Azure single sign-on, as you grant access to the Cisco AnyConnect app.
Step 1. In the app's overview page, select Users and groups and then Add user.
Step 2. Select Users and groups in the Add Assignment dialog.
Step 3. In the Add Assignment dialog, click the Assign button.
Configure ASA for SAML via CLI
Step 1. Create a Trustpoint and import our SAML cert.
Step 2. These commands provision your SAML IdP.
Step 3. Apply SAML Authentication to a VPN Tunnel Configuration.
Note: If you make changes to the IdP config you need to remove the saml identity-provider config from your Tunnel Group and re-apply it for the changes to become effective.
Verify
Test AnyConnect with SAML Auth
Step 1. Connect to your VPN URL and input your login Azure AD details.
Step 2. Approve sign-in request.
Step 3. AnyConnect is Connected.
Common Issues
Entity ID Mismatch
Debug Example:
[SAML] consume_assertion: The identifier of a provider is unknown to #LassoServer. In order to register a provider in a #LassoServer object, you must use the methods lasso_server_add_provider() or lasso_server_add_provider_from_buffer().
Problem: Generally means that saml idp [entityID] command under the ASA's webvpn configuration does not match the IdP Entity ID found in the IdP’s metadata.
Solution: Check the entity ID of the IdP’s metadata file and change the saml idp [entity id] command to match this.
Time Mismatch

Debug Example:
[SAML] NotBefore:2017-09-05T23:59:01.896Z NotOnOrAfter:2017-09-06T00:59:01.896Z timeout: 0
See Full List On Docs.microsoft.com
[SAML] consume_assertion: assertion is expired or not valid
Problem 1. ASA time not synced with IdP’s time.
Solution 1. Configure ASA with the same NTP server used by IdP.
Problem 2. The assertion is not valid between the specified time.
Solution 2. Modify the timeout value configured on the ASA.
Wrong IdP Signing Certificate Used
Debug Example:
[Lasso] func=xmlSecOpenSSLEvpSignatureVerify:file=signatures.c:line=493:obj=rsa-sha1:subj=EVP_VerifyFinal:error=18:data do not match:signature do not match
[SAML] consume_assertion: The profile cannot verify a signature on the message
Problem: ASA not able to verify the message signed by the IdP or there is no signature for the ASA to verify.
Solution: Check the IdP signing certificate installed on the ASA to make sure it matches what is sent by the IdP. If this is confirmed, make sure that the signature is included in the SAML response.
Invalid Assertion Audience
Debug Example:
[SAML] consume_assertion: assertion audience is invalid
Problem: IdP is defining the incorrect audience.
Solution: Correct the Audience configuration on the IdP. It should match the ASA’s Entity ID.
Wrong URL for Assertion Consumer Service
Example Debug: Unable to receive any debugs after the initial authentication request is sent. The user is able to enter credentials at IdP but IdP does not redirect to ASA.
Problem: IdP is configured for the wrong Assertion Consumer Service URL.
Solution(s): Check base URL in configuration and make sure it is correct. Check ASA metadata with show to make sure that the Assertion Consumer Service URL is correct. In order to test it, browse it, If both are correct on the ASA, check the IdP to make sure that the URL is correct.
SAML Configuration Changes Not Taking Effect

Example: After a single sign-on URL is modified or changed, the SP certificate, SAML still does not work and sends previous configurations.
Problem: ASA needs to regenerate it's metadata when there is a configuration change that affects it. It does not do this automatically.
Solution: After making changes, under the affected tunnel-group remove and re-apply the saml idp [entity-id] command.
Troubleshoot
Anyconnect Vpn Client Download Windows 10
Most SAML troubleshoots involve a misconfiguration that can be found when the SAML configuration is checked or debugs are run. debug webvpn saml 255 can be used to troubleshoot most issues, however in scenarios where this debug does not provide useful information, additional debugs can be run:
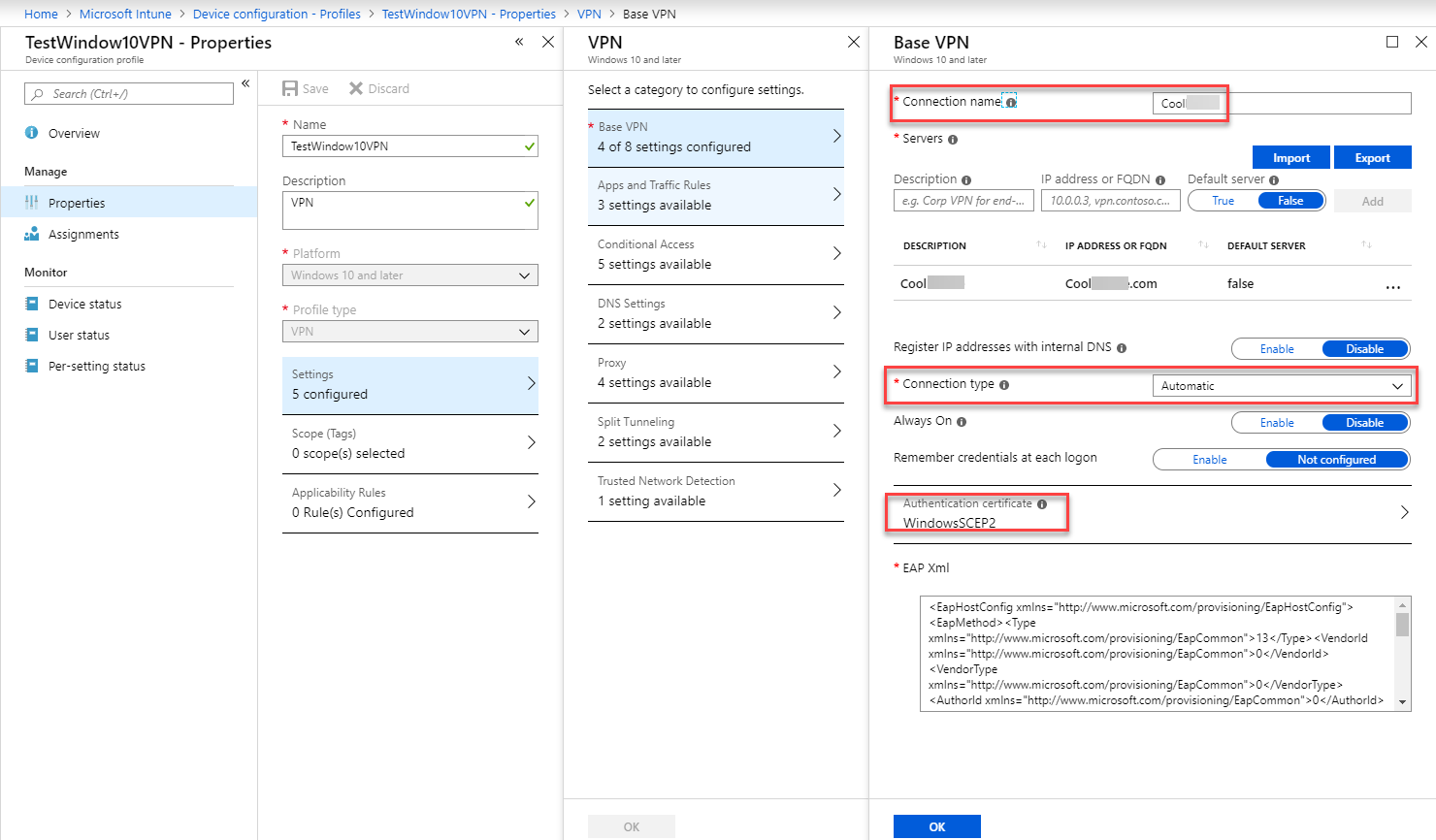
Cisco Anyconnect Intune Windows
Related Information
